A Shenzhen blogger tweeted that provincial authorities ordered him to delete a post about potential man-in-the-middle (MITM) attacks involving the China Internet Network Information Center (CNNIC):
省政府新闻办打电话来称,“谷歌称CNNIC发布中间人攻击证书”一文需要立刻删除。
— 月光博客 (@williamlong) March 26, 2015
The provincial government news office called to say that I have to immediately delete the article “Google Says CNNIC Issues Certificates for Man-in-the-middle Attacks.”
The post is gone from @williamlong’s blog, but is still available from Google’s cache and CDT Chinese.
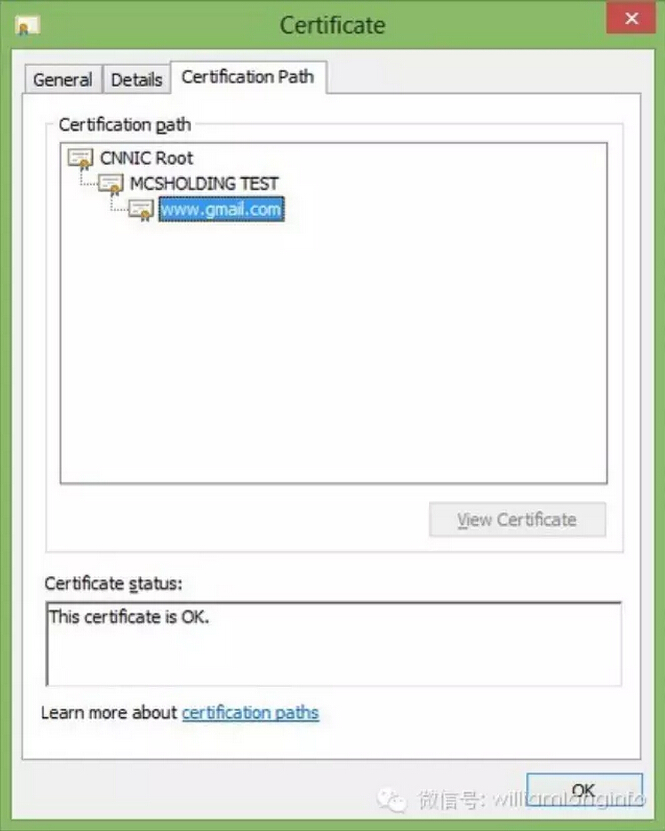
Late last week, the CNNIC issued a temporary certificate to the Egypt-based Mideast Communication Systems (MCS). Its subsequent misuse threatened to compromise the certification system used for authentication and encryption across the web. On Monday Google and Mozilla reported that they had detected and blocked the certificate. Mozilla explained its potential impact:
An intermediate certificate that is used for MITM allows the holder of the certificate to decrypt and monitor communication within their network between the user and any website without browser warnings being triggered. An attacker armed with a fraudulent SSL certificate and an ability to control their victim’s network could impersonate websites in a way that would be undetectable to most users. Such certificates could deceive users into trusting websites appearing to originate from the domain owners, but actually containing malicious content or software. We believe that this MITM instance was limited to CNNIC’s customer’s [i.e. MCS’s] internal network. [Source]
CNNIC administers China’s Internet infrastructure, including its domain name registry. Although a non-profit, it is overseen by the Cyberspace Administration of China (CAC), the government agency in charge of Internet policy and headed by “cybertsar” Lu Wei. Censorship monitors Greatfire.org claimed that the MCS revelation constitutes “concrete proof from Google that CNNIC (and by extension CAC) is indeed complicit in MITM attacks,” a possibility it has warned of in the past, and commented on Twitter that “the GFW has switched from being a passive inbound filter to be an active, outbound one.”
CNNIC, though, maintains that:
1.CNNIC has not issued any certificate for the MITM attack. Google’s online security blog has not accused CNNIC for issuing certificates for the MITM attack either. Reports made by some media are inconsistent with the facts.
2.MCS, a server certificate partner of CNNIC, has confirmed that the sub-ordinate certificates improperly issued were only used for internal tests in its laboratory, which is a protected environment.
3.CNNIC has revoked its authorization to MCS on March 22nd.
4.CNNIC reserves the right to take further legal actions. [Source]
A detailed but clear explanation of the issue by Paul Ducklin at Naked Security suggests that MCS’ actions were more irresponsible than malicious. He concludes that “it’s unlikely any direct harm was done.” But as Google security engineer Adam Langley wrote, “CNNIC still delegated their substantial authority to an organization that was not fit to hold it.”
More broadly, Ars Technica’s Dan Goodin commented:
The incident underscores two fundamental weaknesses with the currently implemented system the entire Internet relies on to encrypt sensitive data and to prove websites and e-mail servers belong to the people or organizations claiming ownership. First, with hundreds of authorities directly or indirectly trusted by all major OSes, all it takes is one rogue or lax CA to compromise the security of the entire system. Second, once that security has been compromised, there is no sure way to revoke certificates short of each OS or browser maker issuing its own update. […] [Source]