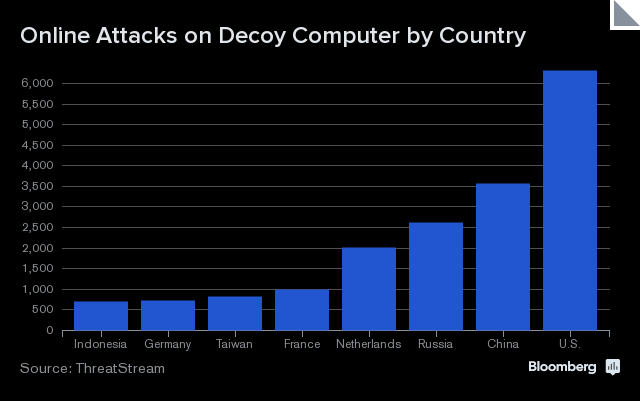
At Bloomberg News, Jordan Robertson describes an experiment involving a decoy “industrial-control” computer, and analysis of the cyberattacks it attracted. The largest number of attacks by far (6,000) came from the United States, with China (3,500) in a distant second place. “A large amount […] if not all of them” are believed to have come from military organizations. The findings appear to provide some vindication for Chinese claims that the U.S., not itself, is the world’s leading cyber-rascal, but Robertson reports that the location data is inconclusive.
That said, the data largely reflect reconnaissance missions, in which hackers often use less obfuscation, Martin said. These probes to learn about networks don’t set off the same alarms that attempts to break into the targets do, so reconnaissance data can reveal many true IP addresses and countries of origin. Nation-states also sometimes launch attacks from bots within their own borders because the government controls the Internet providers, he said. More than anything, the experiment shows that the U.S. is the conduit for a lot of the world’s attack traffic, even if it’s not the source of all of it. And a lot of other countries have their hands in the honeypot as well, as nation-states and private firms race to find the latest vulnerabilities in critical infrastructure.
[…] The honeypot idea was inspired by work that Kyle Wilhoit, a threat researcher at the security firm FireEye, previously did where he replicated the network of a municipal water system that looked like it was in Ashburn, Virginia, population 44,000. The virtual utility was raided within weeks by what Wilhoit said he believes was a Chinese military hacking unit, which stole passwords, engineering PDFs and other data. A later version of the experiment saw hackers, most of them in China, override controls in fake water plants in Europe and Asia. [Source]
Read more about cyberattacks via CDT.