GreatFire.org’s Percy Alpha reports the discovery of malware-infected software on Apple’s Chinese App Store, including Wechat, two NetEase apps, and the DiDi ride sharing app. The attackers dodged Apple’s inspection process by going further upstream and distributing a modified version of the company’s software development tool, Xcode, known as XcodeGhost. Xcode is usually obtained directly from Apple’s Mac App Store, but because large cross-border downloads can be slow and unreliable in China, in large part because of the government’s Internet controls, many users there turn to potentially unsafe unofficial sources.
This is a significant compromise of Apple’s app store. Apple notoriously manually reviews all app submissions and, in comparison to Android stores, has been relatively malware-free. This is the most widespread and significant spread of malware in the history of the Apple app store, anywhere in the world.
[…] It is important to note that the two Netease apps are official apps from Netease. Netease is one of the biggest internet companies in China. Wechat is the most popular messaging app in China. China Unicom is one of China’s major telecom companies and CITIC is one of the country’s largest banks. These apps are likely to be extremely popular and highly trusted by users. It is extremely irresponsible for developers in those companies to ignore digital signature warnings and to continue to use compromised Xcode. If the malware author did a targeted attack against wechat or CITIC, he would have been able to gain users credentials, collect chat history, contact list or even banking details!
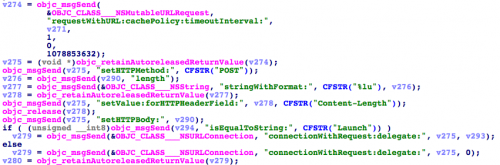
[…] It seems that this particular malware is being used to collect device information for data mining. However, the malware could have been used more aggressively to collect private information such as contacts, photos, and even iCloud passwords via phishing when combined with other evasion mechanisms (link is external) to counter manual reviews. [Source]
According to Palo Alto Networks’ technical analysis, the currently compromised apps gather mostly innocuous data including the time; infected app’s name and bundle identifier; the name, type, UUID, and language and country settings of the device; and the type of network to which it is connected.
At Wired, Joseph Cox talked to Charlie Miller, a security researcher who evaded the App Store’s safeguards in 2011:
“You might completely trust the app developer, and that developer might be completely trustworthy, but this is a case where the app wasn’t,” Miller said. That, and the fact that software made from a tampered version of Xcode found its way onto the App Store, should give developers pause.
[…] But what about consumers, and the people who downloaded the malicious apps? They should be only slightly concerned. “I wouldn’t worry too much,” Miller says. The apps that did get through didn’t seem to do any really nasty stuff. “If you made it really, obviously bad, probably [Apple] would catch it,” Miller says.
The bottom line for customers is, if you’ve downloaded one of these dodgy apps, delete it, and keep up with reports of other ones slipping through. What should developers do to protect their own apps and their customers?
“The moral of the story is: don’t download random crap from Chinese sites,” Miller says. [Source]