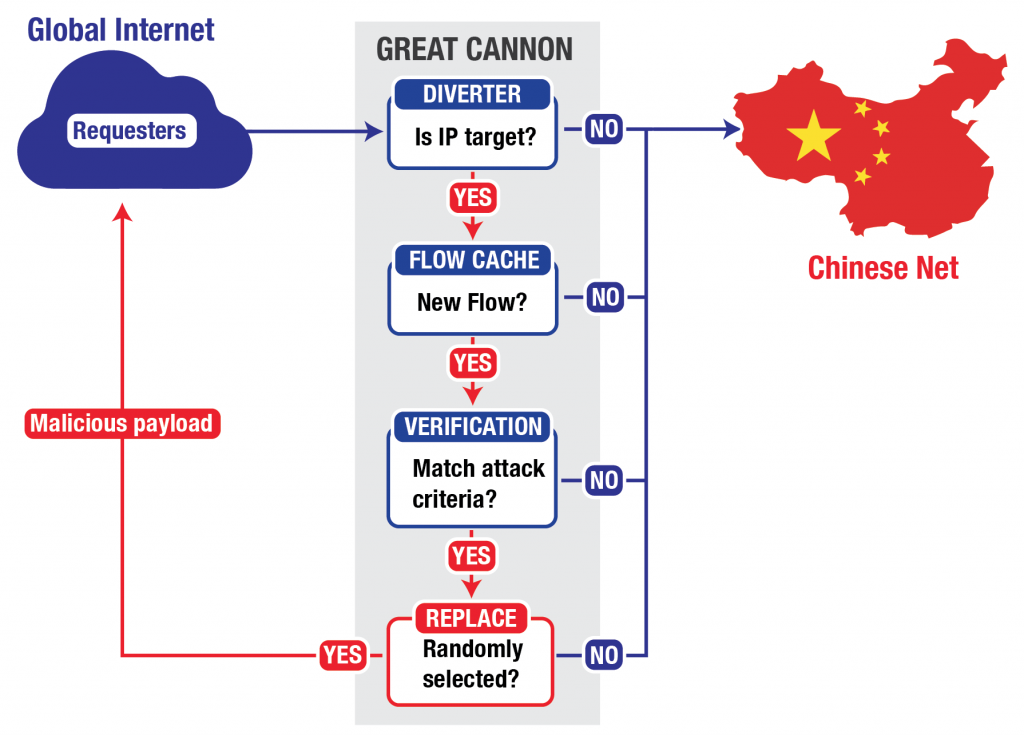
Last month, the censorship monitoring and circumvention project GreatFire.org was the target of two major Distributed Denial of Service (DDoS), including one aimed at the code-sharing site GitHub which hosts two of the group’s pages. Visitors to some Chinese sites from outside the country were unwittingly “weaponized” in an effort to swamp servers with bogus traffic. This hijacking appeared to take place as traffic entered China, crossing the Great Firewall.
On Friday, researchers based at the University of Toronto’s Citizen Lab, the International Computer Science Institute, the University of California at Berkeley, and Princeton University reported that the attacks were conducted using a potent new tool, dubbed “the Great Cannon.” They describe the weapon as separate from the Great Firewall, but say that the two systems’ shared code and network location help compellingly link it to the Chinese government. From Nicole Perlroth at The New York Times:
China’s new Internet weapon, the report says, is similar to one developed and used by the National Security Agency and its British counterpart, GCHQ, a system outlined in classified documents leaked by Edward J. Snowden, the former United States intelligence contractor. The American system, according to the documents, which were published by The Intercept, can deploy a system of programs that can intercept web traffic on a mass scale and redirect it to a site of their choosing. The N.S.A. and its partners appear to use the programs for targeted surveillance, whereas China appears to use the Great Cannon for an aggressive form of censorship.
[…] Still, the Chinese program illustrates how far officials in Beijing are willing to go to censor Internet content they deem hostile. “This is just one part of President Xi Jinping’s push to gain tighter control over the Internet and remove any challenges to the party,” said James A. Lewis, a cybersecurity expert at the Center for Strategic Studies in Washington.
[… Co-author Bill] Marczak said researchers’ fear is that the state could use its new weapon to attack Internet users, particularly dissidents, without their knowledge. If they make a single request to a server inside China or even visit a non-Chinese website that contains an ad from a Chinese server, the Great Cannon could infect their web communications and those of everyone they communicate with and spy on them. [Source]
Co-author Nicholas Weaver explained his impressions of the findings on Twitter:
https://twitter.com/ncweaver/status/586493780926148608
(“Man in the Middle.”)
https://twitter.com/ncweaver/status/586493999650738176
https://twitter.com/ncweaver/status/586494302332661760
https://twitter.com/ncweaver/status/586495074873118720
U.S. law enforcement and intelligence officials, as well as those in other countries, have made repeated calls for measures to allow them access to encrypted data. Critics say this would leave privacy and security dangerously compromised. China has subsequently raised its own demands for “back door” access as a condition for doing business there, citing the U.S. example as justification.
At Krebs On Security, Brian Krebs quoted Weaver and Marczak at greater length on the protection that encryption offers against the Great Cannon:
Weaver said the attacks from the Great Cannon don’t succeed when people are browsing Chinese sites with a Web address that begins with “https://”, meaning that regular Internet users can limit their exposure to these attacks by insisting that all Internet communications are routed over “https” versus unencrypted “http://” connections in their browsers. A number of third-party browser plug-ins — such as https-everywhere — can help people accomplish this goal.
“The lesson here is encrypt all the things all the time always,” Weaver said. “If you have to worry about a nation state adversary and if they can see an unencrypted web request that they can tie to your identity, they can use that as a vehicle for attack. This has always been the case, but it’s now practice.”
But Bill Marczak, a research fellow with Citizen Lab, said relying on an always-on encryption strategy is not a foolproof counter to this attack, because plug-ins like https-everywhere will still serve regular unencrypted content when Web sites refuse to or don’t offer the same content over an encrypted connection. What’s more, many Web sites draw content from a variety of sources online, meaning that the Great Cannon attack could succeed merely by drawing on resources provided by online ad networks that serve ads on a variety of Web sites from a dizzying array of sources. [Source]
HTTPS encryption depends on digital certificates issued by bodies including the government-supervised China Internet Network Information Center (CNNIC). In another cybercontroversy last month, CNNIC certificates were blocked by Google and Mozilla, developers of the Chrome and Firefox web browsers, after the Center “delegated their substantial authority to an organization that was not fit to hold it.” (CNNIC denounced Google’s decision as “unacceptable and unintelligible,” urged the company to “take users’ rights and interests into full consideration,” and censored related news online.)
CNNIC’s role in the certification system would in theory allow it to compromise HTTPS’ protection against the Great Cannon. The cost and likelihood of detection, however, would be high:
@ncweaver doesn't encryption fail to stop MITM if the injector has a valid cert, as could be the case in China? Honest question.
— Richard Bejtlich 💾 🇺🇦 (@taosecurity) April 10, 2015
https://twitter.com/ncweaver/status/586589431978532864
(“Certificate Authority.”)
@ncweaver Ok, so it's technically possible to MITM HTTPS, but, once detected and addressed by the browsers, it's a bad long-term idea. Tks!
— Richard Bejtlich 💾 🇺🇦 (@taosecurity) April 10, 2015
Weaver continued:
https://twitter.com/ncweaver/status/586496134115233792
https://twitter.com/ncweaver/status/586496699062812672
https://twitter.com/ncweaver/status/586554769440776192
The attack’s apparent brazenness might conceivably not have been a top-level decision. China’s cyber forces appear extremely diverse in terms of organization, discipline, and skill. (Weaver himself commented on “stupidities” in the Great Cannon’s design.) Their actions are not always closely coordinated, and their identities not always effectively concealed.
On the other hand, Israeli cybersecurity expert Yael Shahar told The National Journal in 2013 that China’s hackers are “very careful not to cover their tracks very well. It’s a projection of power.” The Great Cannon report argues that the scale and significance of the attack suggest high-level approval for what may have been a deliberately public signal: if, as GitHub suspected, “the intent of this attack is to convince us to remove a specific class of content,” then clear attribution would make the message louder and more widely heard, while still officially deniable. From the Citizen Lab report:
It is likely that this attack, with its potential for political backlash, would require the approval of high-level authorities within the Chinese government. […]
The government’s reasoning for deploying the GC here is unclear, but it may wish to confront the threat presented to the Communist Party of China’s (CPC) ideological control by the “collateral freedom” strategy advanced by GreatFire.org and others. The attack was exceptionally costly to GreatFire, according to their public statements, as well as disruptive to the companies that hosted GreatFire content. Such a disruption could be both an attempt to block the operations of an undesirable resource, and a signal sent to other organizations of the potential price tag for this kind of activity. Deployment of the GC may also reflect a desire to counter what the Chinese government perceives as US hegemony in cyberspace.
[…] We remain puzzled as to why the GC’s operator chose to first employ its capabilities in such a publicly visible fashion. Conducting such a widespread attack clearly demonstrates the weaponization of the Chinese Internet to co-opt arbitrary computers across the web and outside of China to achieve China’s policy ends. The repurposing of the devices of unwitting users in foreign jurisdictions for covert attacks in the interests of one country’s national priorities is a dangerous precedent — contrary to international norms and in violation of widespread domestic laws prohibiting the unauthorized use of computing and networked systems. [Source]
At Foreign Policy, Oxford University and China Copyright and Media’s Rogier Creemers commented on the attack’s context in the long-running Sino-U.S. cyberfeud:
At the heart of this attack lie two fundamentally conflicting views of legitimate governance and security in cyberspace. From the Chinese point of view, the Great Firewall is a critical piece of national security infrastructure that protects against relentless attempts by “foreign hostile powers” to undermine the stability of the regime. The avowed mission of GreatFire.org to unblock censored websites is, in that sense, an act of sabotage that impinges on China’s sovereign right of self-determination.
From the Western point of view, GreatFire.org, which not only monitors censorship trends on the Chinese Internet, but also seeks to unblock censored information, is a courageous defender of the online rights and liberties of China’s citizens, as well as of the integrity of the global Internet. From this angle, China’s tactics undermine trust in Chinese businesses and regulators and risk the Balkanization of the web.
[…] One inconvenient truth that the Western side must face is that China has a better bargaining position. Its chief objective is clearly spelled out in its drive for what it calls Internet sovereignty: to ensure that everything that might affect the Chinese Internet is under Beijing’s control. China’s government doesn’t care whether the Internet balkanizes; in fact, China has no overall transformative goal for the global Internet. Rather, it seeks to govern the international aspects of cyberspace on the basis of 19th century diplomatic principles. Instead of trying to develop a highly complex and new multi-stakeholder model for cybergovernance, it simply assumes a statist model. This defensive posture means that its objectives are much more closely matched to its abilities than the transformative views espoused in the global Internet governance community, which lacks the tools to bring non-compliant countries or organizations into the fold. And China has been able to buttress its position by leveraging its huge domestic market, requiring that global multinationals play by the government’s rules, or not at all. [Source]