A leaked internal document from Xiaohongshu reveals how the Instagram-like social media and e-commerce company deals with censoring discourse about “sudden incidents” on its platform. The document is part of a hundred-plus-page trove that details how the company censors its users in compliance with Beijing’s commands. Last week, we published a partial translation of 546 derogatory nicknames for Xi Jinping, compiled over the course of two months, that was included in the leak.
The document on “sudden incidents”—an official designation for accidents, natural disasters, and political disturbances—is titled “Public Opinion Monitoring System & Management Procedures,” and reveals both what Xiaohongshu considers sensitive and the process by which it censors it with “no omissions.” It begins with a detailed and expansive list of incident types likely to require special treatment. The list include carjackings, landslides, the “Two Sessions,” illegal cult activity, outbreaks of disease among livestock, labor strikes, geographic discrimination, public criticism of the Chinese Communist Party, student suicides, and even the introduction of products that might compete with Xiaohongshu for its user base’s eyes—seemingly blurring the line between censorship and anti-competitive practices. Sudden incidents that occur in Shanghai and Beijing are treated with extra scrutiny. A note underneath the list reads: “If a sudden incident is confirmed to have occurred in Beijing or Shanghai, report it to the Government Relations Team [1] immediately.”
The document goes on to detail the precise mechanisms by which Xiaohongshu quashes discussion of the potential incidents listed above, a process that differs depending on where the censorship order comes from. Censorship directives issued by the Cyberspace Administration of China are to be implemented in “real-time,” whereas internal censorship directives require a response within a comparatively lax five-minutes. In both cases, Xiaohongshu builds new lexicons of “sensitive” words that it keeps on an internal server and “banned” words that it reports to a higher authority, either its Shanghai Operation Security Group or a separate Shanghai-based organization. The lexicon includes derivative variants of both “sensitive” and “banned” words.
CDT has translated the document in full:
Public Opinion Monitoring System & Management Procedures
(1) Definition of Public Opinion Monitoring Incidents
- Content that is likely to incite public panic and impact social stability, such as a catastrophic fire at a sensitive location, “mass incidents”, violent criminal cases targeted at specific populations (fatal stabbings, student stabbings, student suicides, child abuse, etc.).
- Incidents that affect public health or safety, such as chemical explosions, terrorist attacks, outbreaks of food poisoning, major industrial accidents, traffic accidents, and other accidents that result in large-scale loss of life or other damages.
- Major natural disasters and epidemics, including catastrophic earthquakes, floods, landslides, cave-ins, and severe outbreaks of disease among people or livestock.
- Trending topics that supervisory departments have ordered to be deleted and that are likely to stir up public sentiment online, such as geographic discrimination (i.e. the “Beijing Grandpa Incident”).
- Major mass incidents, chiefly large-scale illegal gatherings, petitions, appeals, illegal assemblies, marches, demonstrations, labor strikes, student strikes, teacher strikes, merchant strikes, etc.; obstructing railways, highways, bridges, or roads; besieging or physically attacking government employees; breaking into Party, governmental, and other critically important administrative offices; incidents involving beating, smashing, looting, burning, fighting with weapons, and other incidents, including major illegal activities by cults and other outlawed organizations.
- Major criminal and public security cases, including arsons, poisonings, murders, explosions, hijackings, carjackings, shootings, jailbreaks, riots, and large-scale brawls, looting, or property destruction.
- Sensitive societal incidents and expressions of public opinion. Societal incidents that could trigger political or social unrest and threaten national security. Widespread public criticism or suggestions targeted at the Chinese Communist Party and government institutions.
- Competitors’ products (that could impact our platform)
- Regulatory departments (policy-related, exposés about counterfeit cosmetics, etc.)
- Periodic major events (The Two Sessions and the China International Import Expo, for example)
Note: If a sudden incident is confirmed to have occurred in Beijing or Shanghai, report it to the Government Relations Team immediately.
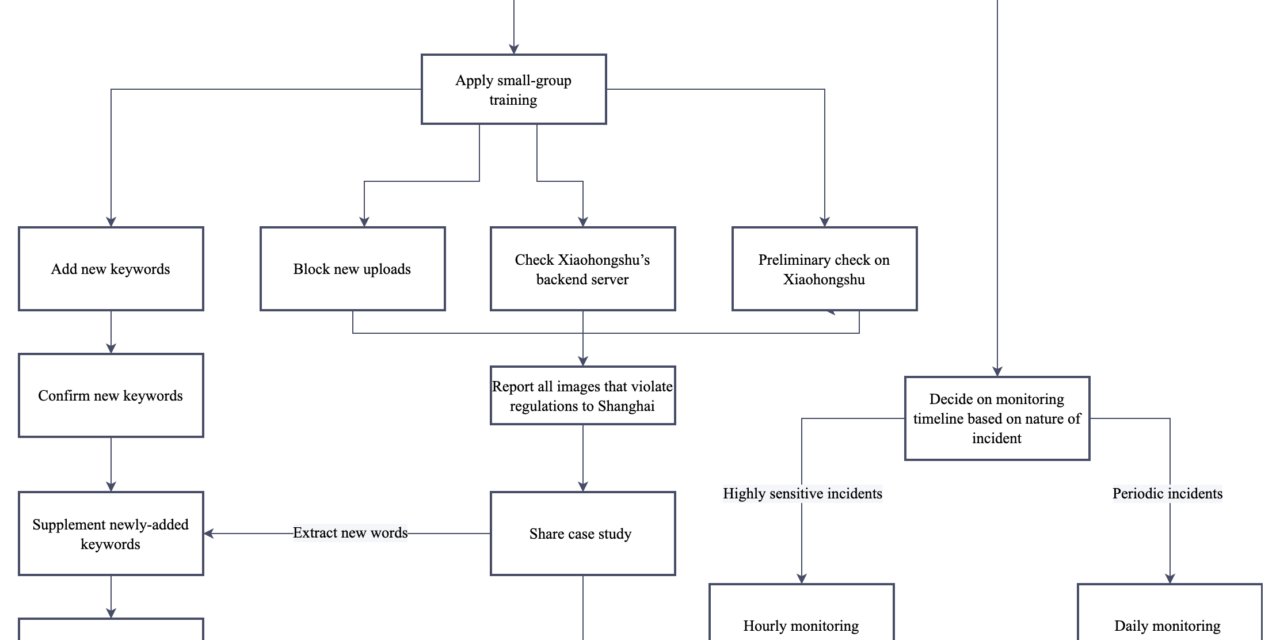
(2) Management Procedures for Sudden Incidents
- Xiaohongshu Internal Procedures for Managing Public Opinion on Sudden Incidents
Note: Report all high-risk incidents to community managers and the Shanghai Operation Security Group within five minutes. For periodic incidents, submit daily reports to community managers and the Shanghai Operation Security Group.
(3) Sudden Incident Response Time
Internal Public Opinion: five-minute response
CAC Directive: real-time response
(4) Requirements for Adding New Keywords
- Quickly extract keywords to add to the sensitive- and banned-words lists (report to Shanghai headquarters) and lexicon of popular terms (for example, place names such as Beijing). Words related to periodic events can be adjusted as events progress.
- Conduct a secondary review to identify derivatives of sensitive keywords, add them to lists, and report to supervisors.
- After keywords have been added, confirm that keyword filters are working during the review process. Report any ineffective filters to the censorship team and provide feedback to the relevant department in a timely manner.
(5) Emergency Review Procedure
- Sudden Incident Management Procedure Following a Directive [from CAC]
Step-by-Step Crisis Response Following a [CAC] Directive
Action
Measures
Step 1Quickly Take Offline 1. Unified review of standards. Team leader designates reviewing personnel. 2. Team leader assigns personnel to conduct immediate review of search-results list for the original title, text, tags, and related videos. 3. Team leader orders a review of popular or widely-used keywords. 4. Apportion keywords among reviewing personnel to avoid duplicated effort. 5. Team leader assigns personnel to add keywords (both sensitive and banned) to the backend. 6. Reviewing personnel begin synchronous review on the backend using Athena. 7. Conduct a secondary review to extract derivative words, and report back to team leader.
Step 2Detailed Screening 1. Apportion derivative words among reviewing personnel to avoid duplicated effort and add to backend keyword warnings. 2. Conduct synchronous review on Athena backend. Search and retrieve based on granular sorting, default sorting, popularity, and time-stamp. Screen based on the number of keyword hits.
Step 3
Final Review1. Perform a secondary review of front- and backend, check results to confirm that keywords are working and that there are no omissions on backend. 2. Compile review data and prepare to report data to supervisors. 3. Summarize review status, iron out any problems, and improve work efficiency.
- Internal Management Procedures for Sudden Public Opinion Incidents
Internal Procedures for Handling Sudden Public Opinion Incidents
Review Procedures 1. Monitor sudden public opinion incidents. 2. Report to supervisors and define standard scale of operation. 3. Team leader sets operational criteria and assigns personnel to conduct immediate review of search-results list for the original title, text, tags, and related videos. 4. Team leader orders a review of popular or widely-used keywords. 5. Apportion keywords among reviewing personnel to avoid duplicated effort. 6. Team leader assigns personnel to add keywords (both sensitive and banned) to the backend. 7. Reviewing personnel begin synchronous review on the backend using Athena. 8. Conduct a secondary review to extract derivative words, and report back to team leader. 9. Apportion derivative words among reviewing personnel to avoid duplicated effort and add to backend keyword warnings. 10. Conduct synchronous review on Athena backend. Search and retrieve based on granular sorting, default sorting, popularity, and time-stamp. Screen based on the number of keyword hits. 11. Perform a secondary review of front- and backend, check results to confirm that keywords are working and that there are no omissions on backend. 12. Compile review data and prepare to report data to supervisors. 13. Summarize review status, iron out any problems, and improve work efficiency. [Chinese]